AWS Certificate Manager Pipelining
This post will walkthrough automating AWS Certificate Manager validation through a Simple Email Service (SES), S3 and Lambda pipeline.
AWS Certification Manager (ACM) requires verification of the ownership of the domain name, or alternatively, of the super-domain of the domain that you want the certificate for.
Currently the only way this is done is through email to the following addresses,
http://docs.aws.amazon.com/acm/latest/userguide/gs-acm-validate. html
- Whois domain, technical, and administrative contact
- The administrator, hostmaster, postmaster, webmaster, and admin addresses at the requested domain (or to the super-domain specified by the validation domain setting).

The SES pipeline method to simplify AWS certificate manager validation. The Cloudformation template will generate an ACM certificate during creation, which will generate a verification email. By setting up SES on that domain, we can forward the email through S3 to a Lambda remailer and out to our real admins. We can also set it up more simply to go to an SNS topic we can subscribe to.
Using the super-domain as the validation domain
With a lot of hosted zones we could end up doing extra work to add MX records
to everyone of them, luckily, we can use the super-domain instead of the actual
domain to do verifications. This means that instead of requiring setting up
mail every hosted zone, we can simply set all the sub-domains to verify on the
super-domain. For example, mysite.mysubdomain.mydomain.com sets validation
domain to mydomain.com, so the verification emails will not be set to
admin@mysite.mysubdomain.superdomain.com, but instead to
admin@superdomain.com.
See the certificate manager user guide for more information.
The cloudformation for certificate manager allows us to set the validation domain through the DomainValidationOptions key.
Domain validation with an external mail server
To achieve this the most straightforward way would be to set up a mail MX record in route53 for your super-domain pointing at your existing mail service, then, when validating the sub-domain, set the validation domain to the super- domain.
Domain validation using SES
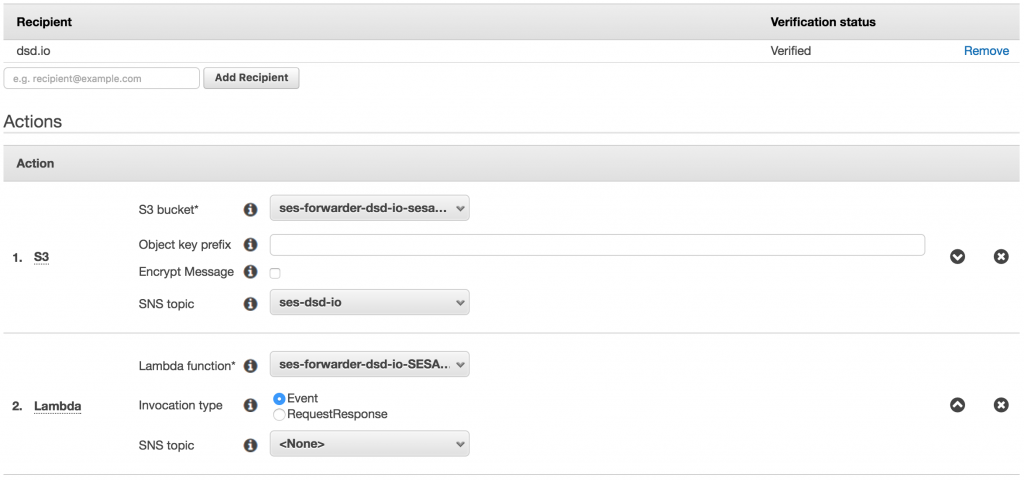
We can set up Amazon Simple Email Service (SES) to work together with ACM. First we setup a route 53 MX record on the super-domain hosted zone to use the Simple Email Service (SES). Add an SES ruleset that sends mail to an S3 bucket and triggers a Lambda function that will forward the email from the bucket. This way the verification email can be sent on to real administrators.
Using the SESLambdaForwarder cloudformation stack
There’s a cloudformation template available for doing this, see https://github.com/niallcreech/cloudformation-seslambdaforwarder.
When creating this stack you can set the email addresses to forward, and a set of forwarding addresses. This cloudformation sets up a lambda function and a S3 bucket with default 3 day deletion policy. We need to setup SES on the domain we want to receive mail on since it doesn’t have cloudformation support, but luckily this is straightforward.
Setup SES on the base domain
-
Create an SES domain for the base domain name superdomain.com
-
Let the SES domain creation set route 53 entries for verification and MX, eg in the superdomain.com hosted zone, superdomain.com MX 10 inbound−smtp . eu−west−1.amazonaws.com
-
Create a SES rule et to send emails to the S3 bucket.
-
When creating certificates, use superdomain.com as the validation domain, this means admin@superdomain.com will be emailed when we create any sub-domain something.somewhere.superdomain.com
-
While the stack requiring an ACM SSL certificate is being created, the forwarding addresses should all receive a validation email
